Case Study - Securing PaaS
Contents
Securing PaaS whiteboard design session student guide
Abstract and learning objectives
In this Case Study, you will work with a group to design an end-to-end PaaS solution that combines many of Azure’s security features, while protecting sensitive data from both internal and external users.
At the end of this Case Study, you will be better able to design secure PaaS-based solutions that protect your systems and data from both internal and external threats.
Step 1: Review the customer case study
Outcome
Analyze your customer’s needs.
Customer situation
Fourth Coffee is an American coffeehouse chain that was founded in Seattle, Washington in 1970. It currently operates over 20,000 locations worldwide.
Victoria Gray, CEO of Fourth Coffee, has established a mandate to revamp their loyalty program that starts with their platform. Currently they provide gift cards that customers can purchase in-store and use at any of their locations. These gift cards can be “re-loaded” with funds by payment by the customer as an in-store transaction. Other than tracking the serial number of the gift card, its balance and purchase history, Fourth Coffee does not have any direct way to associate the purchase history with the customer. They feel this is a big opportunity for them to address, and in doing so will enable them to launch their worldwide customer loyalty program.
They would like to enable their customers to register online to associate any gift cards with their profile. Customers should be able to self-manage their gift card collection, check balances and in the future, receive loyal customer benefits like free coffees or offers to try some of the newest bakery items. At this time, Fourth Coffee is not concerned with enabling customers to “re-load” their cards online. In addition to gift card management, Fourth Coffee would like to enable logged-in users to provide reviews about Fourth Coffee products. They like the idea of coupling reviews to actual gift card users and see a future in which they might reward frequent reviewers with bonus funds on their registered gift cards. These reviews would need to be publicly available and free-text searchable from the website.
In designing and implementing this solution, Fourth Coffee is very concerned about security. They had already launched a customer profile microsite alongside their primary website in Azure using Azure App Services, they host the website in a Web App and all logic is provided thru an API App. They would like to keep this core approach for the gift card website but extend it as appropriate with other Azure PaaS services.
The current customer profile microsite is built with ASP.NET Identity Providers and stores the customer logins and passwords in Azure SQL Database. This was sufficient when the only functionality this site provided was effectively opt-in/out of promotional emails. Now that they will be storing more sensitive information about the customer, they would like to revisit this approach.
A primary concern for Fourth Coffee is figuring out how to secure access to this sensitive data, particularly to limit and control access by their developers. They have put together a “solution security” team who works in the office of the CISO (Chief Information Security Officer) that should be the only group allowed to view the secrets and keys used in production. The developers have expressed concern that this separation of duties, while admirable, is not possible and will prevent them from getting their job done or make it difficult to troubleshoot issues in production.
In addition to securing access to sensitive data, they would like to gain visibility into the security health of their solution. They need guidance on how to they should make sense of all the logs, events and metrics available from the Azure services and are curious if there is anything that can help them monitor their security posture and identify potential issues automatically.
They would like to start designing a pilot solution for one region, that if successful, they could deploy globally down the road.
Customer needs
-
Safeguard and manage identity of users and services.
-
Detect and respond to identity-based threats.
-
Detect and respond to threats to their applications and solutions.
-
Gain visibility into security health.
-
Secure the loyalty data at rest and in transit. Allow access only to those who have a need.
-
They want to achieve the right balance of security versus complexity.
-
Security centered around PaaS services.
### Customer objections
-
Can we really set it up, so our developers’ applications have access to the connection strings, keys and other secrets at run time, without enabling the developers themselves to access this sensitive data?
-
We’ve been told over and over again that Azure’s services, like Azure SQL Database and Azure Storage, must always have a public endpoint. Is that really true?
-
We heard the announcement about Managed Service Identity. We recognize it is in preview now, but we would like to understand how it would improve the security of the solution you are recommending to us.
-
We need to be certain that all of our data is encrypted when it is stored on disk, is that possible with the PaaS services you are recommending?
Infographic for common scenarios
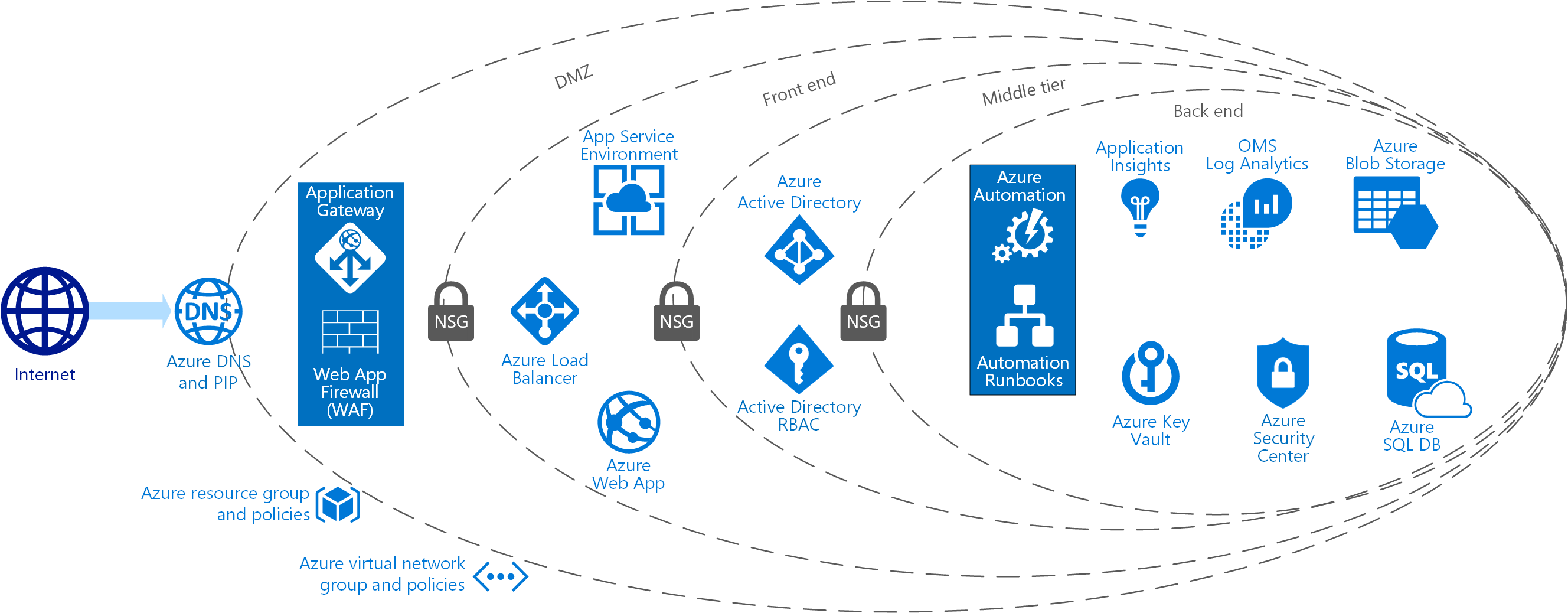
Step 2: Design a proof of concept solution
Outcome
Design a solution and prepare to present the solution to the target customer audience in a 15-minute chalk-talk format.
Timeframe: 60 minutes
Business needs
Directions: Answer the following questions:
-
Who should you present this solution to? Who is your target customer audience? Who are the decision makers?
-
What customer business needs do you need to address with your solution?
Design
Directions: Respond to the following questions:
High-level architecture
-
Without getting into the details, (the following sections will address the particular details), diagram your initial vision for handling the top-level requirements for the gift card website, gift card API, and the storage for customer profiles and transactions. You will refine this diagram as you proceed.
-
What data would you consider sensitive in this scenario? Is there a compliance standard that you would recommend Fourth Coffee consider building their solution against?
Securing customer identity
-
Fourth Coffee mentioned a desire to improve how they manage and store the identities of their customers, for use when granting them access to their online profiles. What approach would recommend they take to modernize their identity management?
-
Would the approach you suggested still allow customers who do not want to use social accounts to create a login with Fourth Coffee?
-
One of Fourth Coffee’s biggest frustrations with their existing identity management approach is that when customers forget their password, they typically must contact support, which is an expensive interaction for Fourth Coffee. How would your proposed solution improve this situation? What would be the process?
Securing the core website components
-
The Fourth Coffee website should be publicly accessible, but the gift card API should not be accessible from the Internet. Additionally, all traffic flowing through to the website should pass through some kind of firewall to guard against malicious requests like cross-site scripting and SQL injection, and the website itself should never be directly accessible in any other way. How would you accomplish this?
-
Fourth Coffee does not like the fact that their existing SQL Database deployment, which contains sensitive customer personally identifiable data (PII), has an endpoint that is accessible on the Internet. They have the firewall rules configured on the SQL Database Server to restrict access, but they would prefer a solution that does not have such a publicly exposed endpoint. What would you suggest and how would they accomplish this?
-
Fourth Coffee is storing customer purchase history for the long term in Azure Storage blobs. Like their previous concern, they would like to know if they could remove the public endpoint access from Azure Storage, since the transaction data reflects sensitive financial transaction information.
-
The existing API App is deployed with the connection string information to the SQL Database saved in the web.config. Fourth Coffee would like to improve the handling of sensitive configuration. What would you recommend they do and how would they need to change their app to support your recommendation?
Enabling reviews
-
Fourth Coffee wants to be certain that their mini-platform for reviews can scale and are less concerned about securing the data (other than securing access to edit the reviews appropriately). How would you suggest Fourth Coffee deploy the logic for managing and navigating reviews, how would reviews (which could grow to become very large data sets) be stored?
-
Fourth Coffee would like users to be able to search across reviews with free-form text, but also narrow their search by product, date range and number of stars. How would you enable end-users to search thru reviews?
-
How would you secure access to the services you propose in support of reviews?
Securing DevOps
-
Fourth Coffee is trying to think about the complete security of their solution, and one challenge they face is in securing how developers interact with production systems for the purposes of deployments as well as troubleshooting. How would restrict deployments to production Web App or API app from occurring across Internet available endpoints?
-
With this safeguard in place, how will developers perform their deployments?
-
They would also like to restrict what developers can see in the database (in terms of sensitive data like gift card data), what options do they have for this?
Monitoring security health
-
What services would you suggest Fourth Coffee utilize in order to monitor the general health of the solution?
-
What service would you suggest Fourth Coffee utilize to monitor the security health of the solution? What it would it provide for their solution?
Additional references
| Description | Links |
| A reference architecture for building a solution that enables PCI compliance using Azure PaaS services | https://docs.microsoft.com/en-us/azure/security/blueprints/payment-processing-blueprint |
| Securing Azure Key Vault - Documentation on how to separate management and data access capabilities when securing Key Vault | https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault |
| Describes how Cosmos DB is secured | https://docs.microsoft.com/en-us/azure/cosmos-db/database-security |
| How to configure a WAF for an ASE v2 environment | https://docs.microsoft.com/en-us/azure/app-service/environment/app-service-app-service-environment-web-application-firewall |
| VNET Service Endpoints | https://azure.microsoft.com/en-us/blog/announcing-virtual-network-integration-for-azure-storage-and-azure-sql/ |