Security baseline on Azure
Security baseline on Azure Case Study
Abstract and learning objectives
In this Case Study, you will work with a group to design an end-to-end solution that leverages many of Microsoft Azure’s security features.
At the end of this Case Study, you will be better able to design and recommend solutions that help organizations properly secure their cloud-based applications while protecting their sensitive data.
Step 1: Review the customer case study
Outcome
Analyze your customer’s needs.
Customer situation
Contoso Ltd. is a multinational corporation, headquartered in the United States that provides insurance solutions worldwide. Its products include accident and health insurance, life insurance, travel, home, and auto coverage. Contoso manages data collection services by sending mobile agents directly to the insured to gather information as part of the data collection process for claims from an insured individual. These mobile agents are based all over the world and are residents of the region in which they work. Mobile agents are managed remotely through regional corporate offices.
The fundamental workflow for Contoso is as follows:
-
Contoso support staff process the incoming claims, which sometimes requires scrubbing, through the corporate website, and create a work order assigned to a mobile agent in the region of the insured.
-
Mobile agents log in daily to the data collection website and retrieve the list of insured customers they are responsible for visiting. They communicate directly with the insured, schedule a time for a home visit, and ultimately during that visit collect information and input it into the data collection website. The sensitive information collected always includes Personally Identifiable Information (PII) and may include Protected Health Information (PHI) about the insured customer. This data is sent over the public Internet securely over TLS (SSL).
-
When the data collection for an insured is completed, the mobile agent marks the task completed so that the corporate system can process those results.
-
Support staff processes complete work orders and submits results through the corporate website requiring another transfer of sensitive data. They also tend to utilize Microsoft Support when tough issues arise and want to know what options they have to engage and log support activities with VMs and other Azure resources.
Contoso currently hosts their systems at co-location facilities within each geopolitical region and manages all IT operations for the systems. In the United States, they have achieved SOC 1 and SOC 2 compliance and follow required HIPAA regulations to protect PHI. Because of the new European GDPR laws, Contoso must evaluate their computing environments for compliance gaps. Contoso has concerns about maintaining their SOC 2 certification and HIPAA compliance with respect to moving to Azure. They would like to specifically address concerns about regional issues of data sovereignty for sensitive data within the context of the GDPR and want to ensure that if they move to Azure, they will be able to continue to have isolation between components.
In addition to the GDPR compliance requirements, they are expecting significant growth within the United States and abroad. They foresee the need to scale their system and are exploring moving their web applications, corporate and data collection web apps, to Microsoft Azure via lift and shift and other applicable methods to simplify some of the operations management overhead and associated costs, beginning with their U.S. data center and then those in Europe. They would also like to ensure that the corporate website and external facing web apps are sufficiently isolated. Lastly, they want to ensure that resources are created using best practices and that those practices are followed during the resource provisioning process.
Contoso has been using their on-premises SIEM to do most of their auditing and log reporting. They are wondering what options they have to monitor their on-premises and future cloud-based resources. They have thoughtfully tuned their on-premises SIEM to reduce false positives and normalize the metadata across different log types. They are worried about the amount of logs and potential for unnecessary work when they move workloads to Azure.
Jack Tradewinds, the CIO of Contoso Ltd, has heard a great deal of positive news about Azure and its progress in terms of security and compliance. He would like to learn more about the security features and if they can move some of their data and applications away from their on-premises data center. Given his long-standing relationship with Microsoft, he would like to see if Azure can meet his needs.
Customer needs
-
Assure data privacy and protection across all aspects of the system; in transit and at rest.
-
Address issues of data sovereignty with respect to the location of sensitive data.
-
Ability to scale as the company grows and system load increases.
-
Contain hosting and operational costs associated with running the system.
-
Enable method to continually review and assign legal compliance tasks to the appropriate individuals and provide a compliance reporting ability for Azure resources.
-
Enforce subscription owners to configure Azure resources with compliance and security while disallowing the creation of specific resources.
-
Ensure that any cloud-based identities utilize the same on-premises username and passwords and limit any help desk interactions.
-
Limit access to the corporate site to users on the Contoso domain, and continue to support VPN access.
-
Extract all web applications that have configuration or embedded connection strings to a more secure implementation.
-
Migrate current database applications to Azure PaaS solution with the appropriate data backup features implemented to prevent catastrophic data loss due to intentional or unintentional acts.
-
Implement all security best practices on the migrated databases such as encryption at rest and during transport as well as ensure that sensitive data is not exposed to non-admin database users and applications.
-
Ensure network segregation between Azure admin and the lift and shifted web and database tiers.
-
Enable logging across all components (identity, virtual network, virtual machine, web, and database) to support an all-encompassing monitoring solution.
-
Ensure that Azure admins utilize best practices when accessing the Azure virtual machine resources and that all logins are logged for identity theft analysis activities.
-
Ensure ease of use by syncing appropriate admin username and passwords for on-premises and cloud resources.
-
Ensure that only authorized users can access specific Azure resources when logged into the Azure Portal.
-
Setup auditing such that software installs are monitored across Azure virtual machine resources.
-
When specific security events are detected (such as a port scan), allow for the execution of actions to remediate, start the investigative process or prevent further information leakage or damage.
Customer objections
-
Can Azure support the lift and shift of their web and database applications?
-
Is Azure SQL secure enough to host their application databases?
-
Admins are worried that they won’t have the bandwidth to perform deployments of the corporate website and other supporting web applications.
-
Can Azure help contain costs for minimally used costly production and development resources?
-
Does Azure support the ability to allow VPN connections to specific resources?
-
Can Microsoft employees or government entities access our data?
-
How does Azure protect against threats?
-
Does Azure allow enough granular RBAC controls to meet our least privilege needs?
-
Is Azure virtual networking flexible enough to meet our requirements?
-
Can Azure supplement on-premises and third-party SIEM systems for auditing and compliance tasks?
-
What certifications does Azure have and can Azure hosted applications meet the US and European compliance goals?
-
Is Azure flexible enough to support data sovereignty needs and issues like those referenced in GDPR articles?
-
How can we ensure continued SOC 1 and SOC 2 compliance?
-
Does Azure permit penetration testing as a part of a security assessment?
Infographic for common scenarios
This Infographic shows an example of a generic implementation of various security Azure technologies in action that can be used as a reference in your design:
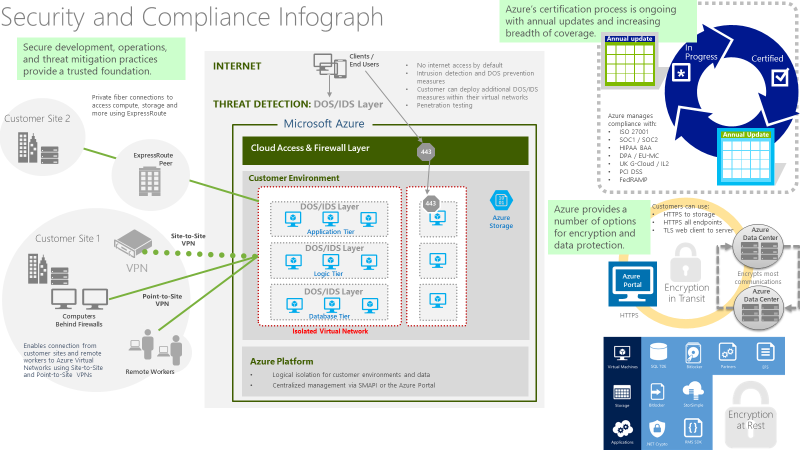
Step 2: Design a proof of concept solution
Outcome
Design a solution.
Business needs
Directions: Answer the following questions:
-
To whom should you present this solution? Who is your target customer audience? Who are the decision makers?
-
What customer business needs do you need to address with your solution?
Design
Directions: Respond to the following questions.
High-level architecture
Briefly sketch-out and propose a high-level solution that meets the customer’s business and technical needs and mitigates their objections. For this workshop, you may choose from the following technologies (you may not need all of them in the correct solution):
-
Azure Virtual Machines and Networks, Network Security Groups
-
Virtual Private Networks (Point to Point, Site to Site) and Express Route
-
Azure Web Apps
-
Azure SQL DB Security Features (Threat Detection, TDE, Column Level Encryption, etc.)
-
Azure Storage Encryption
-
SQL Server 2017 in a VM
-
Azure Security Center, Azure Monitor and Log Analytics
-
Azure Key Vault
-
Microsoft Azure Active Directory (Connect, IAM, etc.)
-
Microsoft Intune
Securing Sensitive Data
On your diagram, indicate how you would secure any sensitive data at rest and in transit with respect to the following:
-
Web Tier (corporate vs. data collection)
-
Database Tier
-
Network, Internal, and External Communications
Ensuring auditing and compliance
Describe how you will use Azure features to ensure the following:
-
How will you monitor and audit VM access?
-
How will you monitor and audit network traffic across Virtual Networks?
-
How will you monitor and audit Azure SQL?
-
Create custom alerts and execute remediation and investigation activities on detection?
-
What tools would you setup to surface audit and for compliance reporting to IT Executives?
Ensuring availability and business continuity
Describe how you would ensure that the following resources would be available in the unlikely event of an attack or intentional or unintentional data loss:
-
Virtual Machines
-
Azure SQL
Ensuring protection
Describe how you would secure each Azure resource from internal and external attacks:
-
Ensure that admin credentials are sufficiently protected and monitored.
-
Prevent admins from causing intended and unintended harm to the environment such as unapproved software installs.
-
Admins access Azure resources from secured and/or compliant corporate assets and do not directly access any production Virtual Machines from the internet.